How Early Positive Experiences Create Well Behaved Dogs
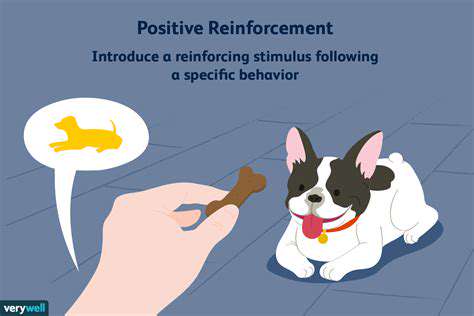
Positive Reinforcement Training: A Comprehensive Overview
Positive reinforcement training is a powerful method for shaping desired behaviors in animals and humans. It focuses on rewarding positive actions rather than punishing negative ones. This approach fosters a positive learning environment, leading to greater cooperation and a stronger bond between trainer and subject.
This method is widely recognized for its effectiveness in achieving long-term behavioral changes. By associating a desired action with a positive consequence, the subject learns to repeat the behavior consistently. This approach is particularly beneficial for animals, as it often results in a more motivated and cooperative learning process.
Key Principles of Positive Reinforcement
At the heart of positive reinforcement lies the concept of rewarding desired behaviors. This involves understanding what motivates the individual and delivering a reward immediately after the desired action is performed. Consistency is crucial; the reward must be consistently given to reinforce the desired behavior.
Identifying and understanding the subject's motivations is essential. What motivates one individual may not motivate another. Therefore, trainers need to be observant and responsive to individual needs and preferences.
Types of Positive Reinforcement
Positive reinforcement can take many forms, ranging from tangible rewards to praise and affection. Treats, toys, or even verbal praise can all be effective reinforcers, depending on the individual and the specific behavior being trained.
Food rewards are often the most straightforward and effective. However, other forms of positive reinforcement, such as praise or petting, can be equally effective, especially for building a strong bond and trust between trainer and subject.
Implementing Positive Reinforcement Effectively
Consistency is paramount in positive reinforcement training. The reward must be given reliably and immediately following the desired behavior. This helps the subject understand the connection between the action and the reward. This consistency allows the subject to learn quickly and effectively.
Careful consideration should be given to the timing and delivery of the reward. The reward should be delivered immediately after the desired behavior to maximize its impact. This close association helps to create a strong association in the subject's mind.
Benefits of Positive Reinforcement Training
Positive reinforcement training offers numerous benefits, including improved learning outcomes, stronger bonds between trainer and subject, and a more positive and productive learning environment. This approach reduces stress and anxiety in both individuals, leading to better long-term results.
Reduced stress and anxiety are key benefits. Punishment-based methods can often lead to fear and avoidance, making learning challenging. Positive reinforcement, conversely, encourages cooperation and a sense of accomplishment.
Addressing Common Challenges
One common challenge in positive reinforcement training is identifying the appropriate reinforcers. What motivates one individual might not motivate another. Careful observation and experimentation are vital to discovering the most effective rewards.
Patience and persistence are essential in positive reinforcement training, as it may take time to see results. It's important to remain positive and consistent in approach.
Measuring and Evaluating Success
Monitoring progress is vital to ensure the effectiveness of the training program. Regular evaluation helps identify areas needing adjustment and celebrates progress. This ongoing assessment ensures the training remains relevant and effective.
Tracking progress allows for adjustments to the training method, ensuring optimal results. This data-driven approach is crucial for fine-tuning the program and maximizing the subject's learning potential.
Building a Secure and Predictable Environment

Planning and Design
A robust security strategy begins with meticulous planning. This involves identifying potential vulnerabilities within the system, outlining specific security measures to mitigate those risks, and defining clear procedures for incident response. A well-defined plan ensures that security considerations are integrated into every stage of development, from initial design to ongoing maintenance.
Careful consideration must be given to the architecture and infrastructure of the system. This includes selecting appropriate security controls and ensuring that the chosen technologies are compatible with the overall security strategy. Understanding the environment's unique characteristics allows for the development of tailored, effective security measures.
Implementing Security Controls
Implementing chosen security controls is a crucial step. This encompasses setting up firewalls, intrusion detection systems, access control mechanisms, and other protective measures. Proper implementation ensures the security measures are correctly configured and actively functioning to prevent unauthorized access and malicious activity.
Regular auditing and testing are essential to ensure that the security controls are effective and up-to-date. This helps identify any gaps or weaknesses in the implementation and allows for prompt remediation, maintaining a strong security posture.
User Authentication and Authorization
Implementing robust user authentication and authorization is vital for controlling access to sensitive data and resources. This involves establishing strong password policies, multi-factor authentication, and roles-based access controls to limit access based on the user's specific needs. This careful approach minimizes the risk of unauthorized access and protects the confidentiality and integrity of data.
Effective user training on security best practices is critical in preventing social engineering attacks and phishing attempts. By raising awareness of common threats, users can be more vigilant and less likely to fall victim to these types of attacks, which often exploit human error.
Data Encryption and Protection
Data encryption plays a critical role in safeguarding sensitive information. Implementing encryption protocols on both data in transit and data at rest ensures that even if unauthorized access occurs, the data remains unreadable without the appropriate decryption keys. This is a fundamental aspect of data protection.
Regular Security Assessments
Continuous security assessments are necessary to identify and address potential vulnerabilities and weaknesses. Regular penetration testing, vulnerability scanning, and security audits help in proactively identifying and mitigating any potential threats. Thorough assessments also help to identify any gaps in the security controls and procedures, allowing for a proactive approach to security.
Incident Response Planning
Developing a comprehensive incident response plan is crucial to effectively managing security incidents. This plan should outline clear procedures for detecting, containing, and recovering from security breaches. It should also include communication protocols for keeping stakeholders informed throughout the incident response process. This proactive approach ensures a swift and organized response to potential breaches, minimizing the impact on the system and mitigating potential damage.
Read more about How Early Positive Experiences Create Well Behaved Dogs
Hot Recommendations
- The Impact of Early Socialization on a Dog's Interaction with Other Animals
- Car Travel and Puppy Socialization: Making the Journey a Positive Experience
- The Importance of Early Environmental Exposure for Puppy Development
- Taking Your Puppy to the Vet: Positive Socialization Strategies
- Making Training a Positive Experience for Your Puppy
- Public Transportation and Puppy Socialization: A Step by Step Guide
- Safe Socialization: Allowing Others to Pet Your Puppy
- Helping a Puppy Who Struggles with "Stay"
- Positive Puppy Interactions: Making Meetings with New Friends Fun
- No Treats Needed? Training Basic Commands with Verbal Praise